Information Security
Information Security

Hanwha Ocean, under our information security management system, implements activities to ensure information security systematically. In particular, we adhere to relevant laws and regulations such as the Personal Information Protection Act and the Act on Promotion of Information and Communications Network Utilization and Information Protection to protect the company’s critical information assets and prevent damages such as data breach and system paralysis due to cyberattacks. To this end, we appoint and report to the Chief Information Security Officer (CISO) under the management organization and operate the Information Security Committee.
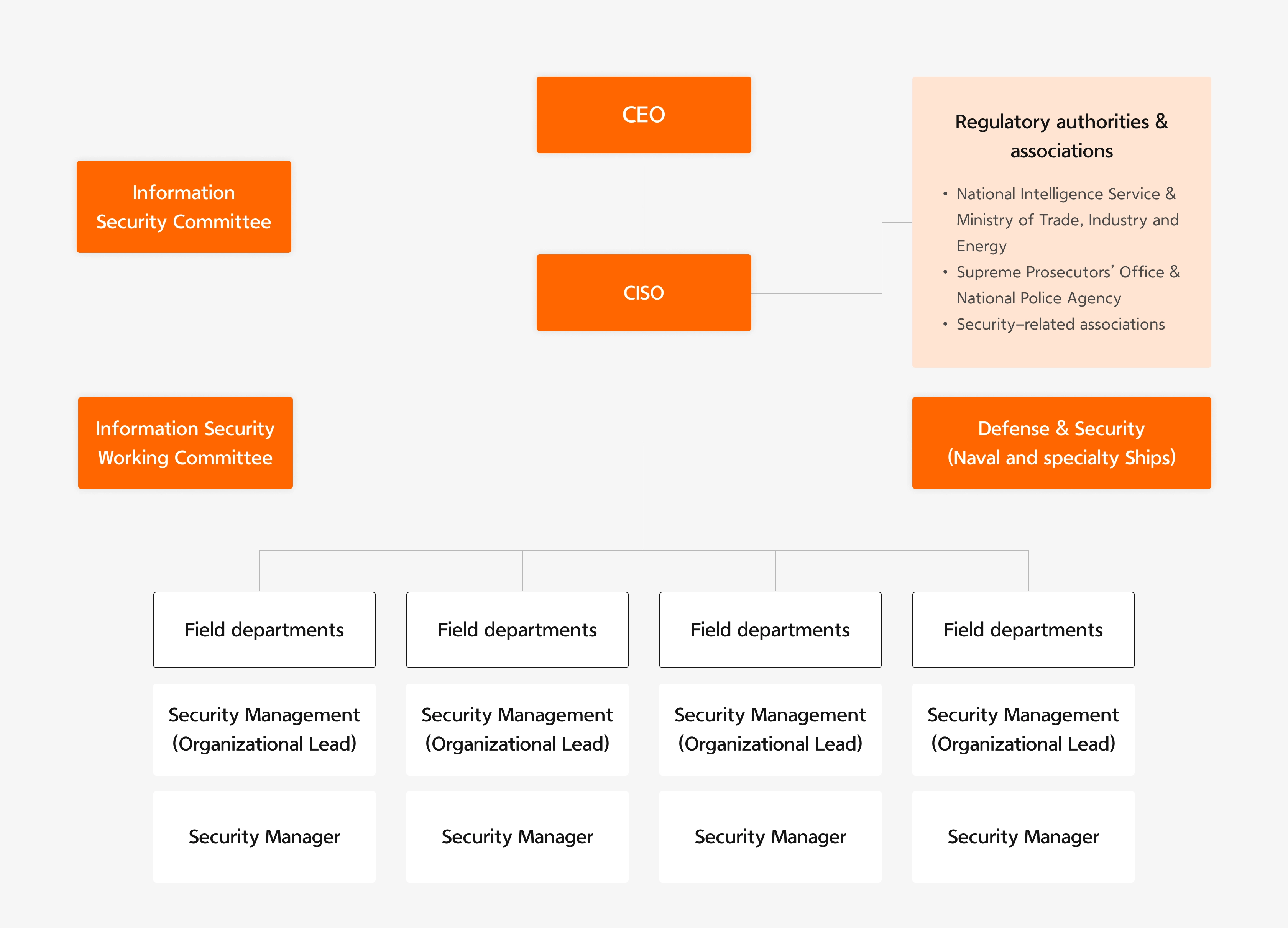
- CEO
- Information
Security Committee -
- CISO
- Regulatory authorities &
associations - National Intelligence Service & Ministry of Trade, Industry and Energy
- Supreme Prosecutors’ Office & National Police Agency
- Security-related associations
- Defense & Security
(Naval and specialty Ships)
- Information Security Working Committee
-
- Field departments
- Security Management (Organizational Lead)
- Security Manager
- Field departments
- Security Management (Organizational Lead)
- Security Manager
- Field departments
- Security Management (Organizational Lead)
- Security Manager
- Field departments
- Security Management (Organizational Lead)
- Security Manager
| Key Decision-making Bodies | Information Security Committee | Information Security Working Committee |
|---|---|---|
| Operating cycle | Operated by the executives meeting presided by the chairperson | Operated on an ad hoc basis when an issue arises |
| Chairperson and responsibilities |
Chairperson : CEO
Roles :
|
Chairperson : CISO
Roles :
|
| Scope of the information security management system | Matters relating to design and production technology information |
Prevention and
Response
Hanwha Ocean has identified leakage of security data by employees and hacking by hacking (spam) mail as major risks, and is strengthening employee education and publicity to prevent them. We designate the first Monday of each month as a company-wide security day, where employees are mandated to read the security training materials to raise their awareness. In addition, we established procedures for reporting spam e-mails, and we conduct mock drills in response to such e-mails to prevent hacking. The results of drills conducted by each department are shared with all employees to raise their security awareness. Additionally, we use the security statement to accurately share company polices and the information assets that need to be protected.
| Phishing e-mails response drills |
PR activities via interactives & Haeoreumteo (internal media) | CEO’s message (security statement) |
|---|---|---|
| 2 | 6 | 1 |
| Classification | 2022 | 2023 |
|---|---|---|
| Infection rate(%) | 2.5% | 7.9% |
| Report rate(%) | 20.8% | 20.5% |

- The company’s confidential information, national core technology, and personal data
- Critical business information generated and managed while carrying out businesses
- Facilities, media, and devices of the information system for providing business support
- Work environment related to physical places and equipment related to business operations
- Establish and implement a security management system to protect tangible and intangible assets.
- Establish and implement administrative, physical, and technical security policies for tangible and intangible assets.
- Establish and implement training plans to enhance the security policy compliance of all employees.
- Establish and implement basic measures for security incident management, business continuity, and regulatory compliance.

Since 2022, Hanwha Ocean has been operating the Hanwha Ocean Cybersecurity Operations Center in cooperation with cybersecurity companies for active security control, real-time threat detection, and systematic response. In addition, to prepare for the increasing number of cyber attacks, we are developing a mid-to-long-term strategy for information security through security consulting. We are also continuing to invest in improving institutional frameworks and maintaining our systems. The following table summarizes the status of our security system by item using information and communications technology (ICT).
| Item | Status of ICT-based Security System |
|---|---|
| Network | We configure firewalls, detect and prevent intrusions, and operate spam-filtering solutions to prevent cyber intrusions at the source; and fundamentally block the access of unauthorized computing devices to the company network. |
| Client | We apply file encryption, printout security solution, and media control to prevent external leakage of the company’s information assets; install antivirus software; block the installation of unauthorized software; and physically separate the network (separation of business network from the internet) in defense zones to avoid data breaches. |
| Integrated security control | We established the Hanwha Ocean Cybersecurity Operations Center to perform security control 365/24/7 together with cybersecurity companies. We also operate a real-time integrated security control system that automates and visualizes data breach and external intrusion control tasks to maximize the efficiency of security control. |
| Subsidiaries and suppliers | We apply the same security policies to all business sites connected via our network (including subsidiaries and internal suppliers) and conduct independent monitoring to block the spread of malware and ransomware. |
As an industry-leading technology company, Hanwha Ocean establishes various policies and engages in diverse activities to comply with international standards and both domestic and foreign law s to protect critical information, including national core technologies. As the foundation for this, we have obtained and maintained ISO/IEC certifications (27001 and 27017), which are international standards for corporate information security management systems.
Training
Hanwha Ocean conducts both online and offline information security training for all personnel, including supplier employees, using various training materials. Shipbuilding, which is our core business, is considered a national core technology. Accordingly, we are required to comply with guidelines under the Act on Prevention of Divulgence and Protection of Industrial Technology. Moreover, we work hard to prevent information leakage not only for new hires but also for security personnel and those scheduled to retire. As for our suppliers, we promote internal security inspection regulations and conduct access control for internal security management.
| Classification | Target | Description |
|---|---|---|
| Offline training | New hires | Industrial security, national core technology, and phishing email simulation training , and access control |
| By job function | Laws related to national core technologies Training in preparation for information security management system certifications (ISO 27001/27017) Phishing email simulation training |
|
| Suppliers | Internal security management, industrial security, national core technology, and access control Promotion of security inspection content related to suppliers |
|
| Online training | By job function |
|
| Distribution of training materials | Security training for national core technologies |